Computer Literacy
Computer literacy is the level of understanding and specialty on computer hardware and software components and the ability to use them in data entry and processing, spreadsheets, word processing, and in performing electronic communications. Computer literacy is not only knowing the basic components, terminologies, and their use but also gaining some core competencies, for instance, learning how to use search engines and identify desired search results (Dubicki, 2013). Computer literate people are also familiar with the word processing tools necessary in the creation of documents, tables, symbols, and composing emails. Computer literacy also entails some networking knowledge of network connectivity, diagnosis, and determining IP addresses. It is also essential to have basic knowledge on the maintenance of a network concerning possible bugs and viruses that may breach the security of the stored data (Dubicki, 2013).
Algorithms
Algorithms are computation set of procedures in a sequence that uses fixed values as input and the given instructions to give other values as the output. Algorithms are significant because they help us in getting solutions to our day to achieve set goals and solve life problems. One of the uses is finding the shortest possible path from point A to point B on a map (Cormen et al., 2009). Algorithms also play a significant role in weather forecasting, making game applications like chess. Algorithms give rise to programs used in the execution of programs necessary in our daily activities like on social media, making online transactions, making animation movies we enjoy, and also accessing information hosted by servers (Cormen et al., 2009).
Technologies That Have Contributed To Exponential Growth of World Wide Web and Internet
The Internet is an extensive network of computers that enhance communication globally. The World Wide Web is an internet tool that has enabled the interconnection of people from various parts of the world. WWW is made up of websites and web pages and is one of the commonly used internet applications in the world. Since the invention of the internet, various technologies have been developed promoting the growth and use of the World Wide Web and the Internet. Some of the technologies that have supported the exponential use of www and the internet for communication and access to information are discussed in this paper (Wich, 2004).
Evolution and Development of Communication Protocols such as the HTML (Hypertext Markup Language) and the URL (Uniform Resource Allocator), HTTP (Hypertext Transfer Protocol), and FTP (File Transfer Protocol)
HTTP enhances efficient retrieval of files, the FTP allows sharing of documents, videos, and pictures allowing upload and download. The technologies have also resulted in the massive development of web pages and websites and allowing people to access them on the internet. There is also the growth in networking technologies enhancing data routing, switching of packets. These technologies facilitate the development of websites and web pages which accessed through hypertext links. The web browser facilities like Mozilla, Chrome, and Opera mini, among others, have also increased people’s accessibility to the web and, therefore, its growth. The growth of database systems such as PHP and ASP to allow easier organization display and data update and linkage to the internet have also played a role in the growth of the WWW. The e-mail technologies that are also some applications of the internet, and the growth in social media platforms like Facebook have also played a prominent role in the growth of the Internet and World Wide Web (Wich, 2004).
Technologies enhancing web-machine interactions through search engines such as Google and Bing have increased communications over the web, enabling the users to add and obtain documents from it. The appearance of the web pages and other contents in websites has changed due to dev elopement of advanced Graphical User Interfaces by adding color to the images and fonts (Wich, 2004). The growth of E-commerce has also resulted in increased growth of WWW since a high percentage of businesses depend on the internet to get clients, payment, and advertising as well. E-commerce has therefore led to the development of complex web architecture to achieve these processes. An increasing number of blogs has also promoted the growth in the use of the web to offer or get information for research business, or entertainment purposes (Wich, 2004).
System Development Life Cycle
The process of developing a system may be complicated and is, therefore, subdivided into sections where specialist architects, analysts, and those in charge of testing the system come together in the System Development Life Cycle (SDLC). SDLC is a process that involves system development, planning, implementation testing and maintenance, and finally disposal to the users. Various models of SDLC contain specified procedures, for instance, the spiral, Rapid Prototyping, incremental, waterfall, among others. The process may be defined in seven steps as described in the following paragraphs (Pathak et al., 2014).
Preliminary Investigation
This is the first phase of the system development life cycle that begins by identifying the need to develop or improve the specified system. A feasibility study, costs, and risk assessments are done in this stage. Other planning activities like assigning roles and responsibilities to the parties involved in the SDLC and setting the necessary policies to be followed are done at this stage (Kay, 2016).
Planning and Requirement Statement
The functional and training requirements are collected, defined and validated. The plans and decisions of the SDLC management in different sectors like operations, configuration, support, and training are also made in the second stage (Pathak et al., 2014).
System Design
The stated functional requirements, features, and training then focus on the system design in detail. The technical details are specified to address the stated functions of the system and a guide on the same is developed (Pathak et al., 2014).
System Development and Testing
Development of the system takes place in consideration of the design specifications and the requirements in this stage. The system is tested on its ability to meet user and business needs. The developed system is validated by integrating it, analyzing its performance, and also testing the system acceptance by the intended users. Also, the procedures used in the development process are documented, tested, and integrated (Pathak et al., 2014).
System Implementation
After developing and testing, the system becomes ready for implementation, and it is installed and introduced to the users through training. The system is incorporated in business to execute the intended purpose; any problems with the system identified are also rectified in this stage (Kay, 2016).
Operation and Maintenance
This step is continuous; the system operations are monitored to ensure that the needs are met continuously without disruptions. Hardware and software maintenance is also done regularly to ensure the efficient running of the system. New features may be introduced in the system to cater to any additional requirements; any reported problems are also addressed in this stage. Constant user support and training are also offered in case of new system users or added features (Pathak et al., 2014).
Disposition
This stage comprises the SDLC process termination, system hardware, software equipment, and codes and documentation are disposed of using the agreed regulations on the matter (Kay, 2016).
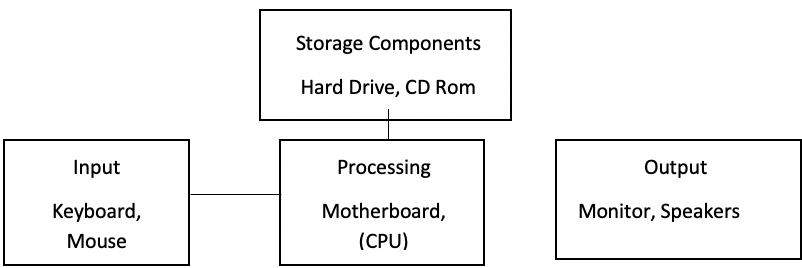
Major Hardware Components in a Computing System
Hardware elements in a computing system may include input-output, storage, or processing devices. The input elements are the keyboard that enters data through typing and a mouse that operates through clicking. Processing device the CPU (Central Processing Unit) accepts the entered data and converts it into information (Berger, 2005). The CPU controls the operations in a computer, including other input and output devices, and performs arithmetic operations. The data entered or processed by a computer may be permanently or temporarily stored by the storage units like the hard drives. Output devices are, for instance, the monitor that displays the code results to the users (Berger, 2005).
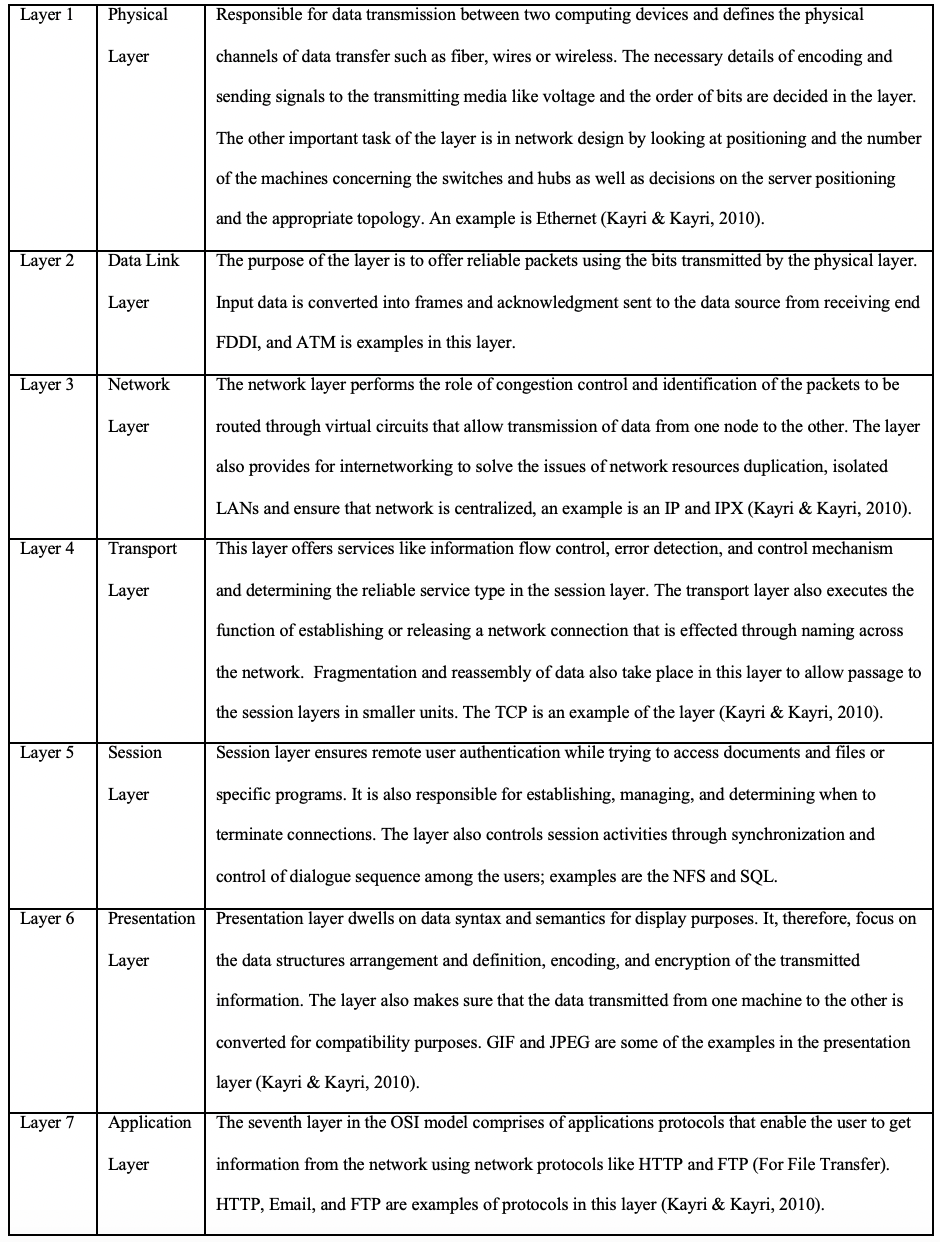
Figure 1
Seven Layers of the OSI Model
The OSI (Open System Interconnection) model breaks down the complex processes and tasks involved in making communications from one computer to another into simpler stages referred to as layers. This section addresses the seven layers of the OSI model beginning with the lowest to the uppermost tier (Kayri & Kayri, 2010).
Table 1
Seven Layers of the OSI Model
Security Concerns Linked to the Internet and Computer Use
The Internet is a valuable resource used to connect different computing devices and enhance communication. However, it also poses some security threats to computing devices. One of the concerns is information phishing that affects hacked websites (Jenkins, 2012). By this, malicious people are likely to access one’s data like online banking and social media accounts like Facebook Hacked sites are also sources of bugs and viruses that can attack computer systems. Internet hackers and crackers use their programming and hardware skills to access information illegally from computer systems over the web and use it for criminal purposes or prove their prowess. The attackers can, therefore, modify or steal private or unauthorized data (Jenkins, 2012). The Internet is also a primary source of computer viruses that spread through downloads or emails accessed over the Internet containing malicious code. These infections may lead to the loss or damage of data. These security threats can, however, be protected by installing antivirus applications in a computer, regular scanning of bugs, constant updates of the security software, and encryption.
References
Berger, A. (2005). Hardware and computer organization. Elsevier/Newnes.
Dubicki, E. (2013). Faculty perceptions of students’ information literacy skills competencies. Journal of Information Literacy, 7(2). http://dx.doi.org/10.11645/7.2.1852
Cormen, T. H., Leiserson, C. E., Rivest, R. L., & Stein, C. (2009). Introduction to algorithms second edition. The Knuth-Morris-Pratt Algorithm.
Jenkins, J. (2012). Internet security and your business – knowing the risks | Symantec Connect. Symantec.com. http://www.symantec.com/connect/articles/internet-security-and-your-business-knowing-risks
Kay, R. (2016). System development life cycle. Computerworld. http://www.computerworld.com/article/2576450/app-development/app-development-system-development-life-cycle.html
Kayri, M. & Kayri, I. (2010). A proposed “OSI based” network troubles identification model. International Journal of Next-Generation Networks, 2(3), 12-18. http://dx.doi.org/10.5121/ijngn.2010.2302
Pathak, M., Verma, B., & Patel, R. (2014). Redefining and extending the scope of system development life cycle: Perspective of today and futuristic human-system interaction environment. International Journal of Computer Applications, 99(17), 37-44. http://dx.doi.org/10.5120/17467-8318
Wich, P. (2004). World Wide Web. Internet-ranking und chemie. Nachr. Chem., 52(2), 165-165. http://dx.doi.org/10.1002/nadc.20040520218


